Mobile App Development: Best Practices from Jain Software
In Business, Official BlogConsidering the present day’s modern world and its rapidly advancing technology, mobile applications are indeed a necessity for everyone. There is no doubt that thanks to the apps, which by now are becoming the most important part of our daily lives we are experiencing a revolution in the way we now use technology in areas like, shopping, banking, health and entertainment. In fact, at Jain Software, we have cultivated a reputation for ourselves that includes the creation of first-rate mobile app solutions that even surpass the expectations of our clients. Here in this blog, I will be writing about some of the things that have been more helpful in mobile application development.
Understanding the User
1. User-Centric Design
Hence, It goes without saying that app development has to be user-based. User experience (UX) is definitely one of the top important factors we focus on from the incubation stage at Jain Software. This is the process of acquiring knowledge on the target clientele’s desires, inclinations and penchant. For surveys, interviews, or usability studies, we gather and analyze quantitative data to know which design to execute.
2. Intuitive User Interface (UI)
The large buttons with a colorful pattern and clear description of functions are essential for the effective user’s interactions and easy navigation. Here, there are honored design principles that are based on the concept of simplicity and clarity. This involves utilizing recognizable icons, standard arrangements of connections, and continuity with other comparable applications. This is achieved with the help of our designers who are closely coordinated with the UX specialists in order to design the interfaces that are both good looking and effective.
Planning and Strategy
3. Clear Objectives and Goals
These principles gratefully require clearer goals and objectives to achieve before breaking down the development process of the app. This includes identifying its role, its objectives towards solving some challenges, and use in enhancing the experience for its users. At Jain Software, it is art of our process to consult the client and gain consensus on the desired vision of the app among all parties involved.
4. Comprehensive Market Research
It is also important to be mentioned that market research is one of the important steps of the planning stage. Such as, evaluating the competition, the threats that may exist and the possibilities of setting up competitive advantage. It assists us in minting the right place for the app and creating functionalities that make the app unique and stand out.
5. Detailed Project Roadmap
The development process should be clearly and accurately outlined so that project participants remain focused on the goal. Therefore, we come up with effective time frames in project development, identify specific goals and timeframes for meeting them and effectively manage resources. This guarantees that each and every the process of development is as effective as possible and timely too.
Development Best Practices
6. Agile Development Methodology
We have applied the classical Agile development model at Jain Software. This kind of approach allows us to provide new information in the form of incremental updates, receive feedback, and modify the strategy as needed to achieve the goals set for the development stage. Agile embraces development of teamwork, dexterity, and gradual enhancement, all of which are instrumental in developing premium mobile applications.
7. Cross-Platform Development
Since the apps are used widely in more than one platform, it may be useful to extend the coverage to multiple platforms. It is important for an app to be developed for both iPhone and Android devices and this can be easily achieved through the help of the development frameworks that include React Native and Flutter. Such an approach allows saving time and resources and also facilitates the definition of the same or similar user experience by different platforms.
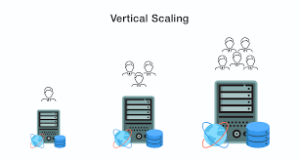
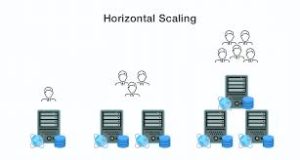
8. Robust Backend Infrastructure
It is crucial in order to ensure that the necessary quality of a good backend is put in place so as to handle the load of requests that the app is likely to generate. Ensuring that your application does not lag regardless of the number of users: We create flexible backend solutions for your application to accommodate more users while sustaining the same level of efficiency as in its early days. The backend infrastructure we designed is adopted to be secure and optimized to store all the data sent by the users and perform all the necessary calculations.
9. API Integration
Android/jave APIs integration proved crucial since they help play a vital role in improving the functionality of mobile applications. Also, the integration of third-party APIs that allow users to implement functionalities such as payment processing systems or social plugin, GPS service, etc. This not only facilitates the interaction but also enhances the feature-set of the application and provides more options for the users.
Testing and Quality Assurance
10. Comprehensive Testing
Availability of reliable test results also makes it easier to diagnose any issues and correct them before they cause major problems that would hinder the use of the app. Functionality testing, performance testing, and security testing and usability testing: All above are done here at Jain Software. This assists in doing an early check to see that everything is properly set before launching the app.
11. Automated Testing
To achieve this, we include the use of automated testing tools so that testing phases can be completed within less time. On the other hand automated testing assist us in detecting as many bugs as possible within a shorter time than when using manual testing, and more importantly when new changes have been made, the tests tell us whether the changes brought new bugs that were not previously present. This in turn helps to advance the cycle and is able to deliver accurate and stable apps.
12. User Acceptance Testing (UAT)
This kind of testing also goes by the name user acceptance testing, which is the last phase of testing where the users test an application in relativity to real life circumstance. After the UAT we obtain the opinions of the end-users and adapt the solution accordingly in case it is necessary to do some changes before its launch. This step is useful to ensure or check if the app is well developed to meet the demands of the users and is fit for the market.
Post-Launch and Maintenance
13. Continuous Monitoring
This is just the beginning, the application release is the first step. To ensure higher effectiveness of the app, respectively the general engagement, and unveil the potential problems when they occur, monitoring should be performed permanently. Analyzing tools help collect such information and enable us to define the behavior of the user regarding the app. This information is vital as it provides us with the data to make decisions for the next updates and enhancements of the site.
14. Regular Updates
Version updates and releases are therefore important for ensuring the applicability of the newly developed app and also for the intention of correcting faults or challenges that may occur. We consult with clients, for prospecting, and make strategies involving updates that may provide new capabilities or make the system more efficient or secure. Other benefits include keeping users busy and active because learning new information is always interesting.
15. User Feedback and Support
The constant flow of feedback from the users is likely to be a crucial factor in the future effectiveness of the app. We would like to make it possible for users to give feedbacks and written reviews especially on areas that they think the websites lacks. To maximize user satisfaction, our support team is always ready to handle different queries that users may come across.
Security Best Practices
16. Data Encryption
Ensuring the privacy of the users and their data is gathering paramount importance. To ensure that all data, especially that of its clients, remains protected, we use different methods of data encryption while data is being transfer as well as when it is being stored. This entails that the user data is not compromised and shared to the wrong quarters through the use of high-security measures.
17. Secure Authentication
Anonymous authentication is inapplicable to contemporary computing systems, but proper access control methods should be applied for the protection of user accounts. Security — we apply MFA and OAuth protocols for the increased protection of accounts. This provides an added security feature, which is an advantage because additional barriers exist in the form of passwords and other forms of identification.
18. Regular Security Audits
Our security solutions are updated on a regular basis and we conduct rigorous assessments of the security system to check for common risks. In an effort to practice adequate security, we perform proper security tests to make sure the app and backend systems are secure. It is also extremely beneficial to be proactive and avoid having the servers vulnerable to certain kinds of attacks that might compromise user information.
Conclusion
At Jain Software we strive to create and provide bespoke mobile app solutions that enhance our client’s product value and usability to their customers. Following best disciplines in user focused planning, development, integration, testing and security makes our applications both effective and compelling, safe. Having worked on hundreds of projects, we have established a team of professionals to provide you with the best that suits your necessities in developing brand new mobile applications or in improving the existing ones. Get in touch with us to improve our mobile app development solutions as well as to discover how our company will be able to assist you in the future.